Hologram Counterfeiting: Problems and Solutions
New Light Industries, Ltd.
Published in Proc. SPIE Vol. 1210, pp. 66-76, Optical Security and Anticounterfeiting Systems, William F. Fagan; Ed. (SPIE Homepage) April 1990.
ABSTRACT
A brief survey of simple hologram counterfeiting techniques and appropriate countermeasures is given and specific cases of successful and unsuccessful counterfeiting attempts are discussed.
1. INTRODUCTION
It is commonly believed that holograms cannot be counterfeited. As a matter of fact, it is rather easy to counterfeit the holograms that are commonly used today in security applications, and holograms have been counterfeited more than once.
There are several straightforward, simple, and inexpensive ways to counterfeit the kinds of holograms currently used in security documents and credit cards. This is not news to the holographic industry, but it may be a revelation to some of the users and potential users of security holograms.
That is the bad news. The good news is that there are countermeasures against hologram counterfeiting which can be extremely effective. Holograms are already well entrenched in the security printing business, and they do add incrementally to the challenge faced by the counterfeiter.
This paper describes the most obvious and effective methods for counterfeiting holograms, and describes a particular holographic security device which appears to be immune to these counterfeiting methods.
2. HOLOGRAM COUNTERFEITING: THE PROBLEM
The problem of hologram counterfeiting includes these aspects:
* the incentive for counterfeiters
* methods, cost, and countermeasures for hologram counterfeiting
2.1 The Incentive for Counterfeiters
If a hologram is the key feature used to judge the validity of an identification card or a product, then the counterfeiter's incentive is directly related to the profits he can make by counterfeiting the hologram. Two examples will suffice to show that the financial rewards to a hologram counterfeiter can be enormous: on the level of tens to hundreds of millions of dollars.
2.1.1 Example 1: Whiskey Labels
Johnny Walker Scotch Whiskey has recently carried a holographic label as a counterfeit deterrent. Roughly 50 million bottles are sold in a year. A bottle of this whiskey costs $16, and the cost of producing a bottle of counterfeit whiskey is less than $2. Assuming volume discounts and markups for middlemen, a counterfeiter stands to make $20 million if he can produce a passable holographic Johnny Walker label.
2.1.2 Example 2: Drivers' Licenses
A driver's license is for all practical purposes the American national ID card. There are several million people in and out of the country who would like to have a California driver's license as fraudulent evidence of U. S. citizenship. Without going into the politics and philosophy of that situation, we can still estimate the financial incentive a potential counterfeiter will have to duplicate the hologram on a driver's license, if holograms are the key security feature on a driver's license.
A good counterfeit driver's license can be worth $500 to $1500. At last count there were over a million illegal aliens in the Unites States. That means there is a potential market in excess of $500 million for counterfeit drivers' licenses.
Clearly, there is a large incentive for potential hologram counterfeiters. This incentive is easily enough to overcome even major technical challenges.
2.2 Methods for Hologram Counterfeiting
The current methods of hologram mastering and embossing were developed in 1980 in a garage in Santa Clara, California on a budget of roughly $9,000. The methods have been widely published, and there are hundreds of individuals and companies all over the world capable of duplicating the methods. Unfortunately, there are much simpler methods available for the counterfeiter.
2.2.1 Mechanical Copying
The simplest method for duplicating an embossed hologram is to use the hologram itself as a mold for producing an embossing die. This is accomplished by removing any adhesive or other coatings from the embossed surface of the hologram, silvering the clean embossed surface, and electroforming a metal such as nickel onto the silver. The electroform is then directly usable as a die for embossing into aluminized polyester or PVC. Counterfeits made this way can be so perfect that no expert will be able to distinguish them from the original hologram.
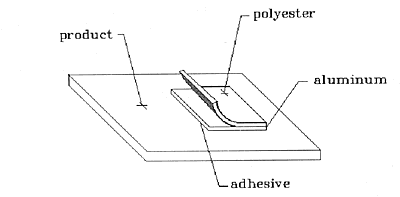
Fig. 1: Typical Holographic Security Label
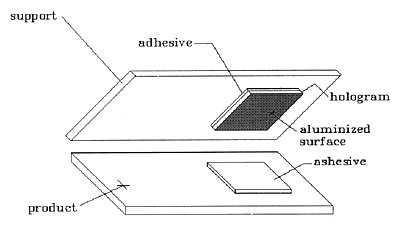
Fig. 2: Removing the Hologram from the Product
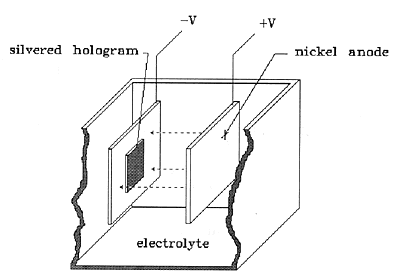
Fig. 3: Electroplating the Hologram
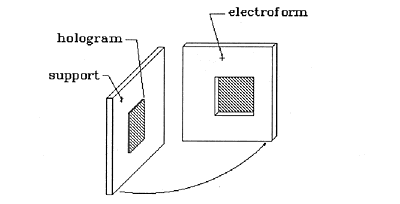
Fig. 4: Separate the Electroform from the Hologram
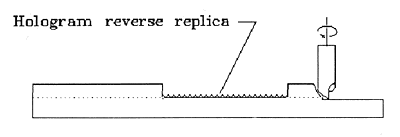
Fig. 5: Trim the Electroform
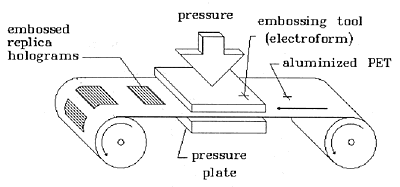
Fig. 6: Use the Electroform as an Embossing Tool
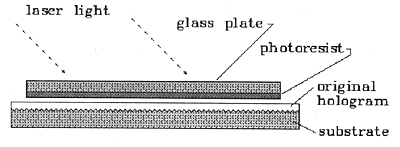
Fig. 7: Contact Copying by Reflection
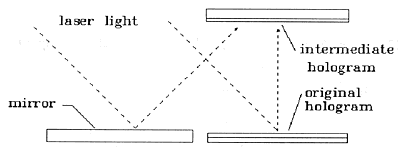
Fig. 8: Two-Step Copying--First-Step
2.2.2 Contact Printing
Almost as simple as mechanical copying is the method of contact printing. In this case, a copy hologram is made by laying a photoresist coated plate in close contact to the original hologram and illuminating the original hologram through the photoresist plate. Diffracted and undiffracted light is reflected from the original hologram and a nearly identical copy is formed on the photoresist plate. The photoresist plate is then silvered and electroplated with nickel; and the nickel plate is used as an embossing die. Counterfeits made by contact printing are similar enough to the original to pass even a close inspection, though with the right tools an expert may be able to detect them.
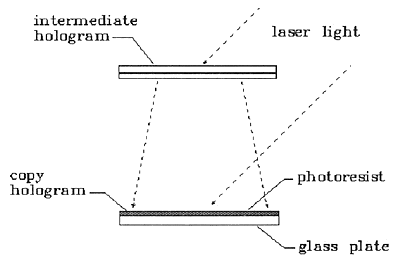
Fig. 9: Two-Step Copying--Second Step
2.2.3 Two-Step Copying
The image in a hologram is optically equivalent to the object from which it was made. It is relatively easy to make a good copy of a hologram by illuminating the hologram with laser light and recording a second hologram of the reconstructed light, then illuminating the second hologram and recording a third hologram using the real image of the first hologram. Counterfeits made by this method are very good. Though an expert with the right tools can detect them, these counterfeits will pass a close inspection by a nonexpert.
2.2.4 Re-Mastering
The technology for making holograms from flat artwork or from solid models is widely known. A hologram made by one manufacturer can be approximately replicated by a counterfeiter by simply recreating the artwork, then making a hologram from the artwork. Counterfeits made by re-mastering are rather easily detected upon close inspection if the artwork is sufficiently complicated or detailed. However, it is very rare that security holograms are subjected to close inspection in actual use.
2.2.5 Simulation
In some cases it is possible for a counterfeiter to acquire commercially available holograms which roughly resemble a security hologram. These simulations will almost never pass even a cursory inspection. However, it is a fact that even crude hologram simulations have been successfully used by counterfeiters. Too often, a clerk will only look to see if there is a hologram on a card, and will not look to see what image is in the hologram!
2.3 Cost and Effectiveness of Counterfeit Holograms
Table 1 shows our estimates of the cost and effectiveness of hologram counterfeiting by the methods discussed above. Effectiveness is on a scale of 1 to 5, with 5 being essentially a perfect copy. Lab cost is the cost of setting up enough equipment to do a good job of counterfeiting. Time is the number of days required to make a counterfeit embossing master from an original embossed hologram. Product Cost is the cost of each embossed counterfeit hologram once the counterfeit embossing master has been made.
| Effectiveness | Lab Cost | Time | Product Cost | |
Mechanical Copying |
5 |
$2,500 |
5 days |
$.05 |
Contact Printing |
4.5 |
$15,000 |
7 days |
$.05 |
Two-Step Copying |
4 |
$20,000 |
10 days |
$.05 |
Re-Mastering |
3 |
$25,000 |
20 days |
$.05 |
Simulation |
1 |
$ 0 |
0 days |
$.25 |
Table 1: Effectiveness and Cost of Hologram Counterfeiting
One interesting feature of Table 1 is that it indicates that the
easiest counterfeiting methods produce the best counterfeits.
2.4 Characteristics that make Holograms Counterfeitable
It is important to examine the characteristics that make holograms easily counterfeitable. Holograms without these characteristics will be much more difficult to counterfeit.
a) non-variable holographic information: i.e., no information in the hologram which depends uniquely upon the content of the document it protects;
b) accessibility of the embossed surface of the hologram to use as an electroforming mold;
c) presence of a nondiffusely reflected portion of the illumination light, substantially stronger than the diffracted portion;
d) unaltered polarization of the diffracted and reflected light from the hologram;
e) ability of the hologram to be reconstructed using standard laser wavelengths;
f) no non-holographic information imposed on the light reflected from the hologram;
g) no large-angle, short wavelength "covert" image features in the hologram;
h) a reasonably uncomplicated image;
i) poor cooperation or communication between legitimate hologram manufacturers;
j) an uneducated or unobservant user base;
k) verification performed by humans.
3. PROPOSED HOLOGRAPHIC IDENTIFICATION CARD
The holographic identification card described below is highly resistant to counterfeiting. In particular, it will inhibit the use of all of the counterfeiting methods that have been discussed here.
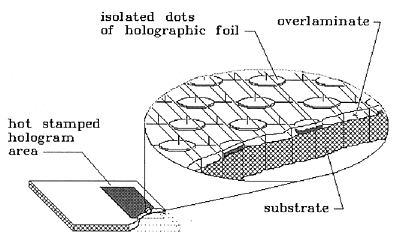
Fig. 10: A Secure Holographic I.D. Card
This card uses a hologram which is hot stamped in a pattern consisting of an array of very small dots(3). Over the hot stamping is applied a coating which bonds to the substrate between the dots. Before the hologram is applied, the substrate is printed with variable information. The hologram itself is a stereogram of a well known human face.
Mechanical copying is effectively prevented because if an attempt is made to delaminate the coating from the substrate, the hologram is left as a large number of isolated dots which are useless as the basis for making an embossing die. Differential adhesion between the hologram dots and the coating to the substrate will make it extremely difficult to remove the coating and the dots together as a single unit, for example to transfer to another card.
Contact copying is effectively prevented because the information printed on the substrate will be recorded in the contact copy. If an attempt is made to make a two-step copy of the hologram, the same problem arises: the variable printed information is recorded at the same time.
A photograph cannot be mistaken for a stereogram because the photograph lacks three dimensionality. As is well known in the security printing industry, a human face is very difficult to counterfeit without detection, so re-mastering the stereogram using a look-alike will be risky. Any good look-alike of a famous person would be rather easy for the authorities to trace.
Re-mastering is made considerably more difficult by the fact that the hologram itself is a stereogram. Aside from the greater complexity of producing stereograms, the use of a well-known human subject will greatly complicate the counterfeiter's task. Re-mastering and simulation are unlikely to be effective because human beings are exceptionally good at recognizing human faces and noticing small differences between them.
4. CONCLUSION
Simple hologram counterfeiting methods and some actual counterfeiting examples have been described, and a new holographic security device has been described which should be immune to the counterfeiting techniques which are effective on most holograms used in security applications today.
It is important to point out, however, that the security of an identification card is based in turn on the security of all of the steps leading from the manufacturer to the user of the card. The steps form a chain, and no chain is any stronger than its weakest link.
There is no evidence to date that any of the manufacturers of security holograms keep accurate records of the number of holograms that are made or shipped, nor that there are accurate records of the number of holograms that are used or rejected by the card manufacturers. There is no serial numbering on holograms. There is no formal association of security hologram manufacturers through which one manufacturer can avoid unintentionally counterfeiting another manufacturer's holograms.
There are several ways to make holograms which can be effective anticounterfeiting devices. However, we strongly urge that hologram manufacturers band together to form an association to provide a basis for cooperation and set standards to improve the security of their products. The best step that users of security holograms can take to ensure the security of the holograms they buy is to insist that their hologram vendors form, join, and support that association.
5. REFERENCES
1. S. P. McGrew, "Countermeasures Against Hologram Counterfeiting," Proc. Optical Security Systems Symposium, Zurich, Oct. 14-16, 1987
2. J. Blyth, private communication
3. S. P. McGrew, U. S. Patent No. 4,589,686 "Anticounterfeiting Method and Device"